Azure App Configuration with Key Vault Integration 🚀
A comprehensive guide to setting up Azure App Configuration with Azure Key Vault for secure configuration management.
Table of Contents 📑
- Overview
- Prerequisites
- Step 1: Create Azure Resources
- Step 2: Add Configuration Values
- Step 3: Integrate with Key Vault
- Step 4: Access Configuration in C#
- References
Overview
This tutorial demonstrates how to:
- Set up Azure App Configuration for centralized configuration management
- Store sensitive data securely in Azure Key Vault
- Use Key Vault references in App Configuration (best practice for secrets)
- Access configuration values from a C# application using managed identity
Prerequisites
- Azure CLI installed and configured
- An active Azure subscription
- PowerShell (commands use PowerShell syntax)
- .NET SDK for the C# code sample
- Appropriate permissions to create Azure resources
Step 1: Create Azure Resources 🏗️
Create Resource Group
Resource groups are logical containers for Azure resources. Use the az group commands to manage them:
az group create --name samples-testmc-rg-itn-01 --location italynorth
az group list -o table
az group delete --name samples-rg-testnc-01 --yes --no-waitCreate Azure Key Vault
Azure Key Vault is used to securely store secrets like connection strings. Create a Key Vault and grant yourself permissions to manage secrets:
$keyVaultName='samples-testmc-kv-itn-01'
az keyvault create --name $keyVaultName --resource-group $resourceGroup --location $location
# Grant yourself access to set secrets
az keyvault set-policy --name $keyVaultName --upn $userPrincipal --secret-permissions get list set delete
Create App Configuration Instance
Azure App Configuration provides centralized configuration management. The following commands register the provider and create an instance in the Free tier:
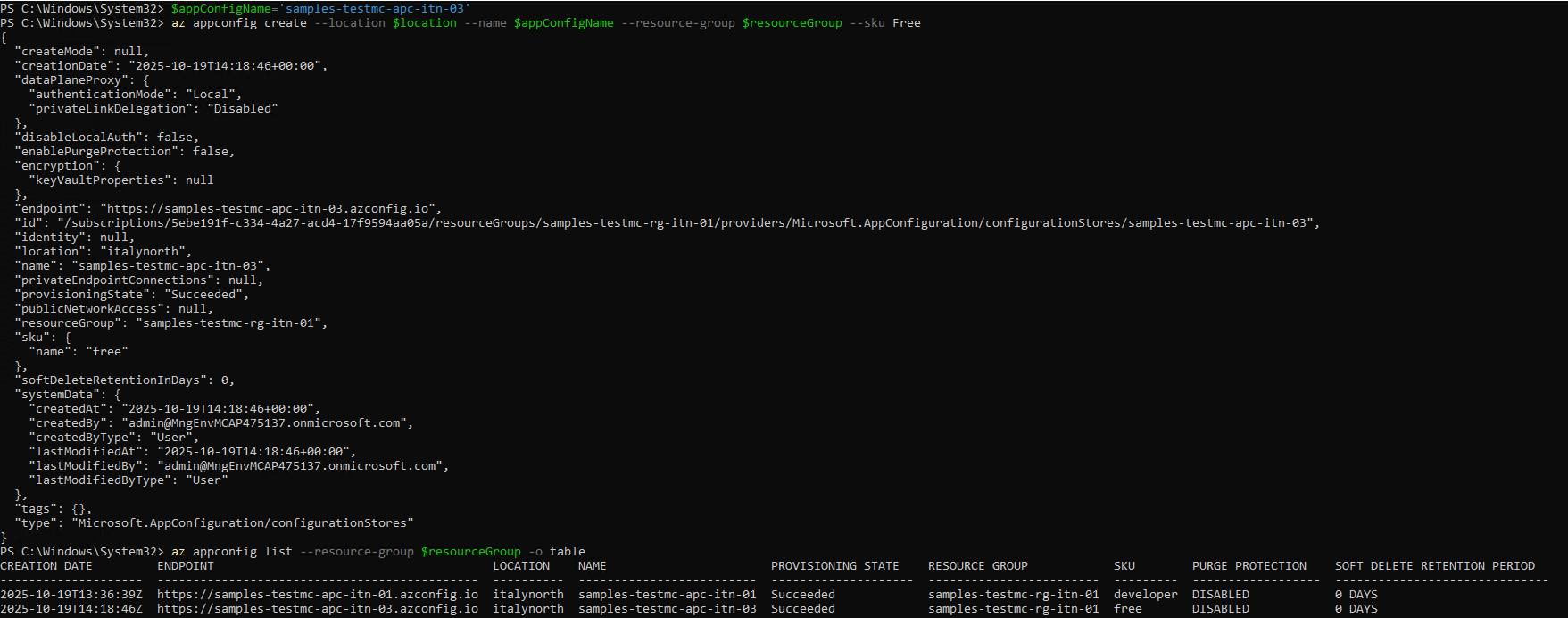
Use az appconfig create to create an Azure App Configuration instance in the Free tier:
$resourceGroup='samples-testmc-rg-itn-01'
$location='italynorth'
$appConfigName='samples-testmc-apc-itn-01'
az provider register --namespace Microsoft.AppConfiguration
az provider show --namespace Microsoft.AppConfiguration --query "registrationState"
az appconfig create --location $location --name $appConfigName --resource-group $resourceGroup --sku Free
List App Configuration instances:
Use az appconfig list to list all Azure App Configuration instances in your resource group:
az appconfig list --resource-group $resourceGroup -o tableAssign permissions:
Use az role assignment create to assign the “App Configuration Data Reader” role to yourself, allowing you to read and manage its settings:
$userPrincipal=$(az rest --method GET --url https://graph.microsoft.com/v1.0/me --headers 'Content-Type=application/json' --query userPrincipalName --output tsv)
$resourceID=$(az appconfig show --resource-group $resourceGroup --name $appConfigName --query id --output tsv)
az role assignment create --assignee $userPrincipal --role "App Configuration Data Reader" --scope $resourceIDStep 2: Add Configuration Values ⚙️
Use az appconfig kv set to add a new configuration setting with key “Dev:conStr” and a sample connection string value to the App Configuration instance:
az appconfig kv set --name $appConfigName --key Dev:conStr --value 'sampleconnectionString' --yes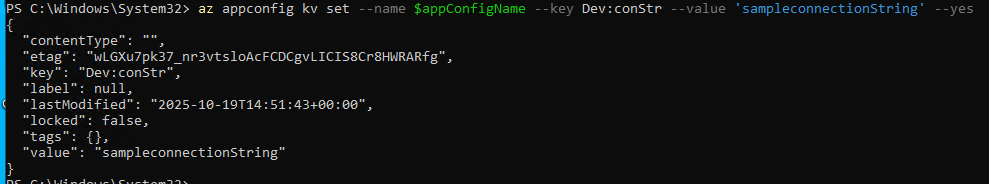
Step 3: add the connection string to Azure Key Vault and reference it from App Configuration
$connectionString='Server=tcp:myserver.database.windows.net,1433;Database=mydb;User ID=myuser;Password=mypassword;'
az keyvault secret set --vault-name $keyVaultName --name 'DevConStr' --value $connectionString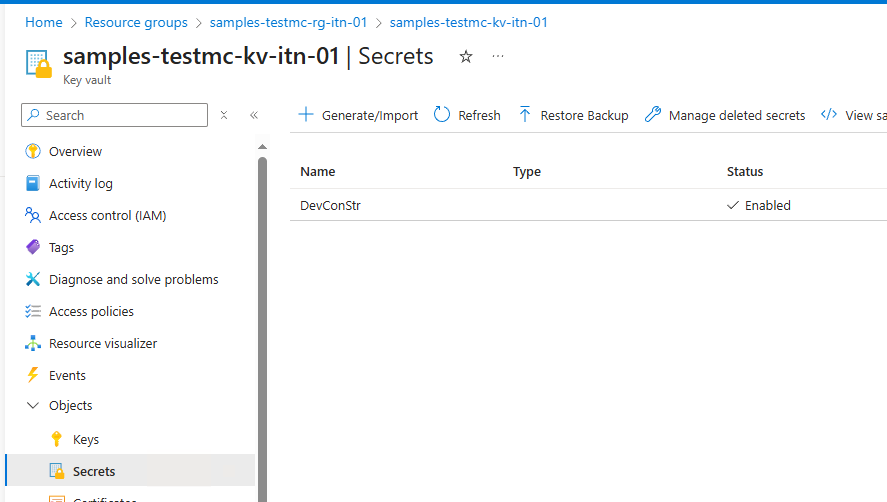
Reference Key Vault Secret from App Configuration
Get the secret URI:
$secretUri=$(az keyvault secret show --vault-name $keyVaultName --name 'DevConStr' --query id --output tsv)Set the App Configuration secret reference to Key Vault:
az appconfig kv set-keyvault --name $appConfigName --key 'Dev:conStr' --secret-identifier $secretUri --yes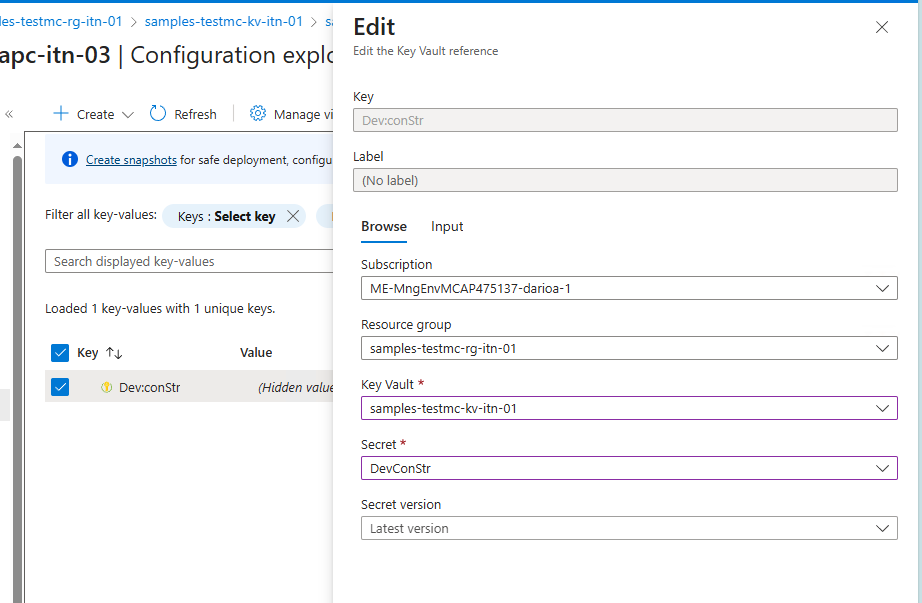
Configure Managed Identity
Enable managed identity for App Configuration:
az appconfig identity assign --name $appConfigName --resource-group $resourceGroup
Get the managed identity principal ID:
$principalId=$(az appconfig identity show --name $appConfigName --resource-group $resourceGroup --query principalId --output tsv)Grant the managed identity access to Key Vault secrets:
az keyvault set-policy --name $keyVaultName --object-id $principalId --secret-permissions getStep 4: Access Configuration in C# 💻
Use builder.AddAzureAppConfiguration to read the configuration value from Azure App Configuration in a C# application:
using Microsoft.Extensions.Configuration;
using Microsoft.Extensions.Configuration.AzureAppConfiguration;
using Azure.Identity;
// Set the Azure App Configuration endpoint, replace YOUR_APP_CONFIGURATION_NAME
// with the name of your actual App Configuration service
string endpoint = "https://YOUR_APP_CONFIGURATION_NAME.azconfig.io";
// Configure which authentication methods to use
// DefaultAzureCredential tries multiple auth methods automatically
DefaultAzureCredentialOptions credentialOptions = new()
{
ExcludeEnvironmentCredential = true,
ExcludeManagedIdentityCredential = true
};
// Create a configuration builder to combine multiple config sources
var builder = new ConfigurationBuilder();
// Add Azure App Configuration as a source
// This connects to Azure and loads configuration values
builder.AddAzureAppConfiguration(options =>
{
options.Connect(new Uri(endpoint), new DefaultAzureCredential(credentialOptions));
});
// Build the final configuration object
try
{
var config = builder.Build();
// Retrieve a configuration value by key name
Console.WriteLine(config["Dev:conStr"]);
}
catch (Exception ex)
{
Console.WriteLine($"Error connecting to Azure App Configuration: {ex.Message}");
}References 📚
Official Microsoft Documentation
- Azure App Configuration
- Azure Key Vault
- Managed Identity
- .NET Integration
- Azure CLI Reference