External User Types and Invitation Process in Azure AD/Entra ID
1 Table of Contents
- 🔑 Understanding External User Types
- 📬 The Invitation and Redemption Process
- ⚙️ Capabilities and Limitations by Identity Type
- ✅ Best Practices for Guest User Management
- 📚 Appendix: Technical Details
- 🔗 References
2 🔑 Understanding External User Types
Azure AD (now Microsoft Entra ID) supports multiple types of external users, each with different characteristics, capabilities, and limitations.
The identity type of a guest user determines how they authenticate and what resources they can access.
2.1 ExternalAzureAD Identity Type
ExternalAzureAD represents the most robust type of external user account.
These users are federated with their home Azure AD tenant and maintain their organizational identity.
Characteristics:
- User Principal Name (UPN):
user@externaldomain.com#EXT#@hostingtenant.onmicrosoft.com - Authentication: Performed against the user’s home Azure AD tenant
- Identity Source: External Azure AD organization
- Federation: Fully federated with the source tenant
How it’s created: This identity type is created when a guest user redeems an invitation using their organizational work or school account from an Azure AD-backed organization. The redemption must occur through Microsoft Entra authentication flow (typically steps 1-5 in the invitation flow diagram).
2.2 Mail Identity Type
Mail identity type represents a simplified guest account that relies on email-only verification without a backing Microsoft or organizational account.
Characteristics:
- User Principal Name (UPN):
user_externaldomain.com@guest.hostingtenant.com - Authentication: Email one-time passcode (OTP) or similar email-based verification
- Identity Source: Email address only
- Federation: No federation with external tenant
📝 Note on UPN Format Variations:
The UPN format for Mail identity type can vary depending on your tenant’s configuration:
Standard Microsoft Format:
user_externaldomain.com#EXT#@hostingtenant.onmicrosoft.com
(e.g.,john_contoso.com#EXT#@fabrikam.onmicrosoft.com)Custom Guest Domain Format:
user_externaldomain.com@guest.hostingtenant.com
(e.g.,john_contoso.com@guest.fabrikam.com)The format shown above reflects a custom guest domain configuration. Some organizations configure custom verified domains for guest accounts for branding, governance, or compliance purposes. The key identifier for Mail identity type is:
- The
@symbol in the original email is replaced with_(underscore)- No federation with the user’s email domain
- Authentication relies on email OTP, regardless of UPN format
How it’s created: This identity type is created when:
- A guest redeems an invitation using email one-time passcode authentication
- The guest doesn’t have or doesn’t use a Microsoft account or Azure AD account during redemption
- The organization has email OTP enabled as a fallback authentication method
2.3 Microsoft Account (MSA) Identity Type
Microsoft Account represents users who authenticate using a personal Microsoft account (e.g., @outlook.com, @hotmail.com, or a personal email registered as an MSA).
Characteristics:
- User Principal Name (UPN):
user_domain.com#EXT#@hostingtenant.onmicrosoft.com - Authentication: Microsoft Account authentication system
- Identity Source: Microsoft consumer identity platform
- Federation: Federated with Microsoft Account system, not an organizational tenant
How it’s created: Created when a user redeems an invitation using their personal Microsoft account credentials.
3 📬 The Invitation and Redemption Process
The invitation redemption process is critical in determining the resulting guest user identity type. Understanding this flow helps administrators ensure guests obtain the correct identity type for their organizational needs.
3.1 Invitation Flow Overview
The invitation process follows these key stages:
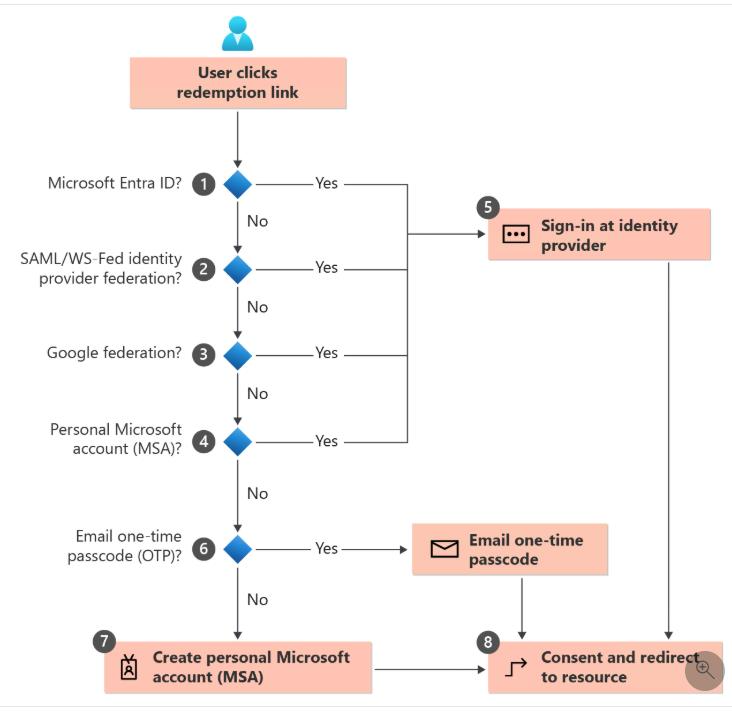
Stage 1: Invitation Creation
- Administrator creates a guest user invitation in Azure AD
- Invitation email is sent to the external user’s email address
- Invitation contains a redemption URL with a unique token
Stage 2: Invitation Email Received
- Guest user receives email with invitation link
- Email typically contains information about the inviting organization
- Link directs to the redemption flow
Stage 3: Redemption Initiation
- Guest user clicks the invitation link
- Azure AD begins the redemption process
- System attempts to identify the user’s existing identity
3.2 Redemption Methods and Their Impact
The diagram illustrates different redemption paths:
Path 1-5: Azure AD Federated Authentication (Recommended)
- User clicks invitation link
- Redirected to Microsoft authentication page
- CRITICAL: User must authenticate with their organizational (Azure AD) work or school account
- Home tenant (e.g., sensorfact.nl) validates the user
- Guest account created with ExternalAzureAD identity type
- Result: Fully federated guest user
- Authentication: Through home organization’s Azure AD
- Identity: Maintains organizational identity
Alternative Path: Email One-Time Passcode
- User clicks invitation link
- User chooses “Use email one-time passcode” or doesn’t have an Azure AD account
- System sends OTP to email address
- User enters OTP code
- Guest account created with Mail identity type
- Result: Non-federated guest user
- Authentication: Email OTP only
- Identity: Email-based, no organizational backing
Alternative Path: Microsoft Account
- User clicks invitation link
- User signs in with personal Microsoft account
- Guest account created with Microsoft Account identity type
- Result: MSA-backed guest user
- Authentication: Through Microsoft consumer identity
- Identity: Personal Microsoft account
3.3 Critical Decision Point: Authentication Method
The key decision point occurs at Step 3 in the flow. The user must:
✅ DO:
- Open invitation in a private/incognito browser window
- Sign in with their organizational work or school account
- Ensure they’re authenticated to their home Azure AD tenant
- Complete the redemption while maintaining that session
❌ DON’T:
- Use email one-time passcode if an organizational account is available
- Sign in with a personal Microsoft account when an organizational account exists
- Accept invitation while signed into the wrong tenant or account
4 ⚙️ Capabilities and Limitations by Identity Type
Different external user identity types have varying levels of functionality within the hosting organization.
4.1 ExternalAzureAD Capabilities
Full Functionality:
- ✅ Microsoft Teams Access: Full Teams application authentication and functionality
- ✅ SharePoint and OneDrive: Complete file access and collaboration features
- ✅ Azure AD Application Access: Can authenticate to Azure AD-integrated apps
- ✅ Conditional Access: Subject to both home and host tenant policies
- ✅ Multi-Factor Authentication (MFA): Honors home tenant MFA policies
- ✅ Single Sign-On (SSO): Seamless authentication across Microsoft services
- ✅ Privileged Access: Can be granted elevated permissions if needed
Security Features:
- Identity managed by home organization
- Password policies enforced by home tenant
- Account lifecycle managed by home organization
- Audit logs available in both tenants
Use Cases:
- Long-term business partnerships
- Regular collaboration on Teams and SharePoint
- Access to line-of-business applications
- Projects requiring compliance and security controls
4.2 Mail Identity Limitations
Limited Functionality:
- ⚠️ Microsoft Teams: May experience authentication failures or limited functionality
- ⚠️ Application Access: Many Azure AD-integrated apps may not authenticate properly
- ⚠️ Conditional Access: Limited ability to enforce complex policies
- ⚠️ MFA: Cannot leverage organizational MFA; relies on email verification only
- ⚠️ SSO: No seamless authentication; requires repeated email OTP entry
- ❌ Privileged Access: Generally not suitable for elevated permissions
Security Concerns:
- No organizational backing or identity management
- Relies solely on email account security
- No password policy enforcement
- Limited audit trail capabilities
- Email compromise = account compromise
Use Cases:
- One-time or very limited access scenarios
- External users without organizational Azure AD accounts
- Simple file sharing without application integration
- Short-term access needs
4.3 Microsoft Account Considerations
Moderate Functionality:
- ✅ Basic Microsoft Services: Can access basic Microsoft 365 services
- ⚠️ Teams and Apps: May work, but not recommended for organizational use
- ⚠️ Security Controls: Limited organizational control
- ✅ MFA: Can use Microsoft Account MFA if configured
Concerns:
- Personal account used for business purposes
- Limited organizational oversight
- Consumer-grade security policies
- Mixing personal and business identity
Use Cases:
- Rare; generally not recommended for business collaboration
- May be acceptable for very casual, non-sensitive scenarios
- Better alternatives usually available (ExternalAzureAD or Mail)
5 ✅ Best Practices for Guest User Management
5.1 Ensuring Proper Identity Federation
For Administrators:
- Pre-Invitation Communication
- Inform guests about the proper redemption process
- Provide clear instructions to use organizational accounts
- Explain the importance of authentication method selection
- Verification Process
- After invitation redemption, verify the guest user’s identity type
- Check the user object in Azure AD for the
userTypeand identity source - Confirm UPN format matches expected pattern for ExternalAzureAD
- Remediation Steps
- If wrong identity type is created:
- Delete the guest user account
- Resend invitation with clear instructions
- Consider having a call with the guest to guide through redemption
- If wrong identity type is created:
- Configuration Settings
- Review External Identities settings in Entra ID
- Configure appropriate authentication methods
- Consider disabling email OTP for scenarios requiring federated identities
- Set up access packages for standardized onboarding
5.2 Troubleshooting Common Issues
Issue: “Account does not exist in tenant” Error
Symptom: Guest user receives error when accessing Teams or Azure AD apps, stating their account doesn’t exist in the hosting tenant.
Root Cause: User account created with Mail identity type instead of ExternalAzureAD.
Resolution:
- Verify identity type in Azure AD user properties
- Delete the existing guest account
- Resend invitation
- Guide user to redeem using organizational account in private browser window
- Verify new guest account has ExternalAzureAD identity type
Issue: Guest Cannot Access Teams Application
Symptom: Authentication failures or access denied when using Teams.
Root Cause: Non-federated identity type (Mail or MSA) attempting Teams access.
Resolution:
- Confirm this is a federated requirement for your Teams usage
- Recreate guest with proper ExternalAzureAD identity
- Ensure Teams licensing and permissions are correctly configured
Issue: Guest User Receives Repeated OTP Prompts
Symptom: User must enter email OTP frequently, disrupting workflow.
Root Cause: User has Mail identity type, causing email-based authentication.
Resolution:
- If user has organizational account: recreate with ExternalAzureAD identity
- If user lacks organizational account: consider if they need extended access
- Evaluate whether a Microsoft Account might be appropriate
5.3 Organizational Policies
Recommended Policies:
- Default Authentication Method
- Prioritize Azure AD federated authentication
- Limit email OTP to specific scenarios
- Document when each method is appropriate
- Guest User Reviews
- Implement regular access reviews
- Verify identity types match access requirements
- Remove or remediate accounts with incorrect identity types
- External Collaboration Settings
- Define which domains can be invited
- Configure collaboration restrictions appropriately
- Balance security with collaboration needs
- Documentation and Training
- Create guest onboarding guides
- Train administrators on identity type implications
- Establish helpdesk procedures for guest issues
6 📚 Appendix: Technical Details
6.1 Appendix A: User Principal Name (UPN) Formats
Understanding UPN formats helps identify and troubleshoot guest account types.
ExternalAzureAD Format:
user@externaldomain.com#EXT#@hostingtenant.onmicrosoft.com- Original email domain preserved:
externaldomain.com - Uses
@symbol before#EXT# - Indicates federation with external Azure AD
Mail/MSA Format:
user_externaldomain.com@guest.hostingtenant.com- Original email domain mangled:
_replaces@ - Uses
@guest.hostingtenant.comdomain suffix - Indicates non-federated or MSA identity
Example:
- Federated:
manon.wientjes@sensorfact.nl#EXT#@abbinternaltest.onmicrosoft.com - Non-Federated:
manon.wientjes_sensorfact.nl@guest.abbinternaltest.com
6.2 Appendix B: Invitation API Behavior
When using Microsoft Graph API or PowerShell to create invitations, understanding the behavior helps automate proper guest creation.
Graph API Invitation Endpoint:
POST https://graph.microsoft.com/v1.0/invitationsKey Properties:
invitedUserEmailAddress: Target email addressinviteRedirectUrl: Where user goes after redemptionsendInvitationMessage: Whether to send email automaticallyinvitedUserType: Typically “Guest”
Automatic Identity Detection: Azure AD attempts to determine if the invited email belongs to:
- An existing Azure AD tenant (will prefer ExternalAzureAD)
- A Microsoft Account (will use MSA)
- Neither (will create Mail identity or use OTP)
Forcing Identity Type: You cannot directly force an identity type during invitation creation. The identity type is determined during redemption based on how the user authenticates.
6.3 Appendix C: Conditional Access and Guest Users
Conditional Access policies interact differently with various guest identity types.
Policy Evaluation:
- ExternalAzureAD Guests
- Subject to both home tenant and host tenant policies
- Home tenant MFA is honored
- Host tenant can add additional requirements
- Device compliance can be evaluated if device is known to home tenant
- Mail Identity Guests
- Only subject to host tenant policies
- Limited MFA options (email OTP only)
- Cannot evaluate device compliance meaningfully
- Risk-based policies may have limited effectiveness
- Best Practice
- Design policies specifically for external users
- Consider identity type when setting requirements
- Test policies with different guest types before deployment
- Document expected behavior for each scenario
Common Policy Scenarios:
- Require MFA: Works best with ExternalAzureAD (can leverage home tenant MFA)
- Require Compliant Device: Only meaningful for ExternalAzureAD guests
- Require Approved Client App: Can work with all types but enforcement varies
- Block Legacy Authentication: Apply to all guest types for security
7 🔗 References
Official Microsoft Documentation:
Azure AD B2B Invitation Redemption
Comprehensive guide to the invitation and redemption processExternal Identities in Microsoft Entra ID
Overview of external collaboration capabilitiesAdd Azure AD B2B Collaboration Users
Administrator guide for inviting guest usersEmail One-Time Passcode Authentication
Details about email OTP authentication methodProperties of an Azure AD B2B User
Technical details about guest user object propertiesConditional Access for B2B Users
Guide to applying Conditional Access policies to external usersCross-Tenant Access Settings
Configuring trust relationships and access settings between tenantsTroubleshoot Azure AD B2B Collaboration
Common issues and resolutions for B2B scenarios
Additional Resources:
Microsoft Graph Invitation API
API reference for programmatic invitation creationExternal Identities Best Practices
Security best practices for external collaboration
Document Information:
- Created: November 2, 2025
- Topic: Azure AD / Microsoft Entra ID External User Management
- Related Issue: Guest Account Login Fail Issue - 20251014
2.4 Social Identity Providers
Azure AD B2B also supports social identity providers (Google, Facebook, etc.) if configured.
Characteristics:
How it’s created: Only available if the hosting tenant has explicitly configured and enabled social identity providers in their External Identities settings.